Identifying A Scam: How to Stay Safe in an Online World
In today’s digital age, scams have become increasingly prevalent, impacting individuals worldwide. From fraudulent credit card charges to hacked email accounts, nearly everyone knows someone who has fallen victim to a scam. This article will break down the most common scams, their tactics, how to identify them, and what steps to take if you are targeted.
What is a Scam?
A scam is a dishonest scheme designed to fraudulently obtain money, possessions, or personal information. While scams have existed for centuries, evolving from pyramid schemes and check fraud to today’s tech-savvy tactics, their ultimate goal remains the same: to take something of value from you.
Modern scams often involve suspicious emails, phone calls, or internet pop-ups, but they can take many forms. Despite the variety, all scams share a financial motive and rely on manipulation to succeed.
Common Types of Scam
Scammers use a wide range of tactics. Here are some of the most common ones:
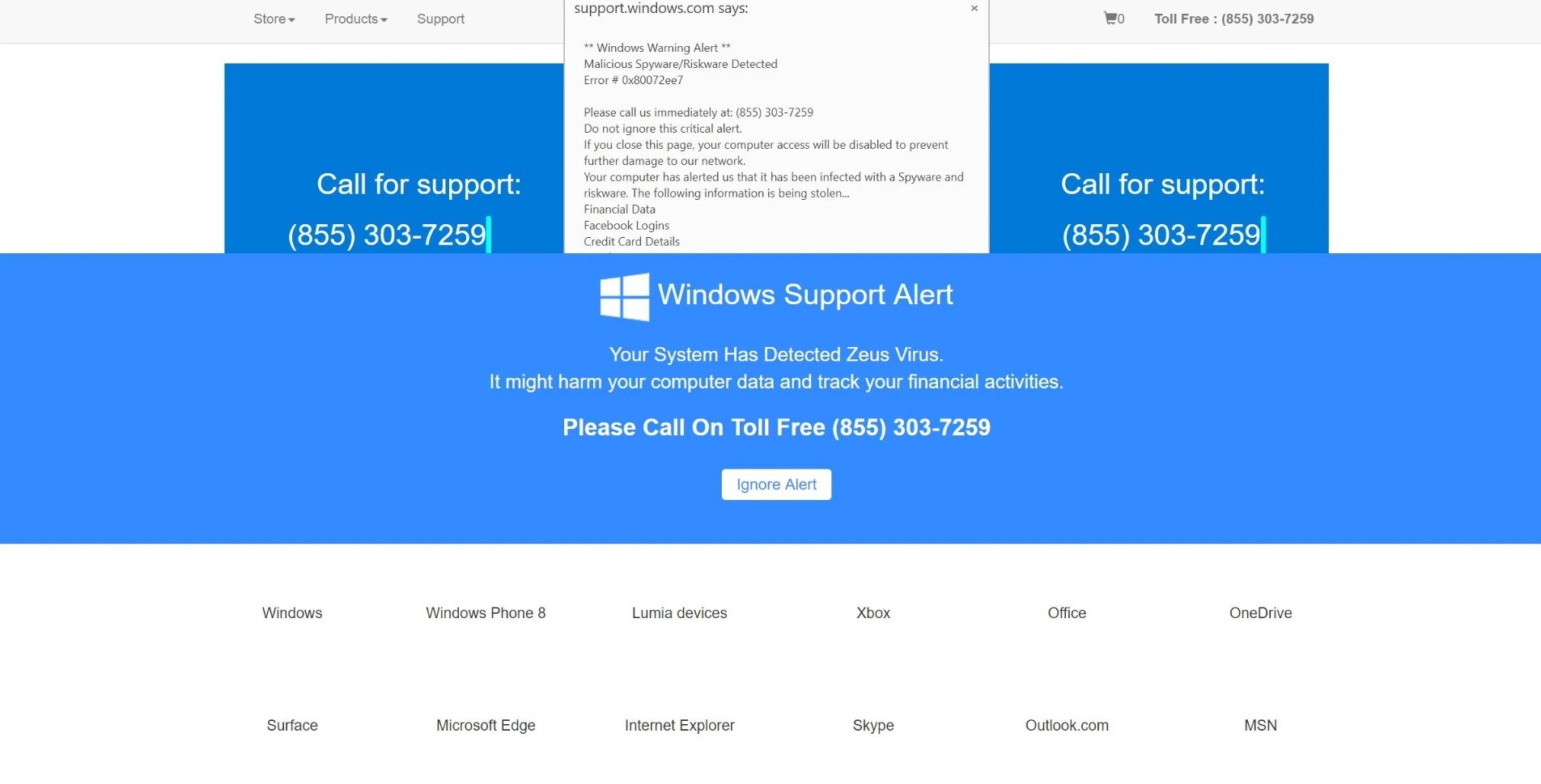
Tech Support
Often appearing as pop-ups claiming your computer is infected, these scams urge you to call a fake support number. The scammers pretend to fix non-existent issues and charge exorbitant fees. These pop-ups are designed to look official, featuring company logos and warnings to create urgency.
Phishing
Phishing scams use fake emails, text messages, or websites to steal sensitive information such as account passwords or credit card details. These messages often appear to come from trusted organizations and urge you to click on a link to log in or provide personal information. The fake sites mimic legitimate ones to trick victims into providing their credentials.
Business Email Compromise (BEC)
Targeting businesses, this scam involves gaining access to a company’s email account, often through phishing. Scammers monitor communications and intercept invoices, altering payment details to redirect funds to their accounts. These scams can go undetected for months, causing significant financial losses.
Romance Scams Romance scams involve fake online dating profiles used to build trust with victims. Scammers often play the "long game," eventually fabricating emergencies that require financial assistance. These scams exploit emotions and can be particularly devastating.
Impersonation - Impersonation scams involve scammers pretending to represent well-known companies, such as Microsoft or your utility provider. They may claim you owe money, need a refund, or require assistance with a security issue. The goal is often to trick you into transferring money or providing sensitive information.
These are just a few of the scams we see the most, there are dozens/hundreds of more that we couldn’t list here and new methods popping up every day.
How To Identify a Scam
Despite their variety, most scams share common traits. Here’s how to spot them:
Examine the Sender’s Email - Check the sender’s email address carefully. Legitimate companies use official domains (e.g., @microsoft.com), while scams often originate from generic addresses like @gmail.com or misspelled variations of official domains. Compare the email address to contact details listed on the company’s official website.
Verify Phone Calls - If you receive a suspicious call, hang up and contact the company directly using a number from their official website. Legitimate organizations rarely make unsolicited calls demanding immediate payment or access to your accounts.
Pause and Reflect - Scammers often create a sense of urgency or fear to pressure you into acting without thinking. Take a moment to step back and assess the situation. If something feels off or overly aggressive, it’s likely a scam.
Consult an Expert - If you’re unsure, seek advice from a trusted tech expert or your local telecom store. Many professionals are happy to help identify scams and provide peace of mind.
What to Do If You’ve Been Scammed
Even the most vigilant individuals can fall victim to scams. Here are the steps to take if it happens to you:
Disconnect Immediately - If you suspect someone has access to your device or account, turn off your computer or hang up the phone to prevent further action by the scammer.
Contact Your Bank - Notify your bank or financial institution right away. They can freeze your accounts to stop further transactions and guide you on the next steps.
Sanitize Your Devices - Have your devices professionally inspected by a tech specialist. Depending on the circumstances, you may need to back up important files and reset your device to ensure it is secure.
Reset Your Passwords - Change the passwords for all compromised accounts. Use strong, unique passwords for each account and update any similar passwords to prevent further breaches.
Report the Incident - Report the scam to your local police or a fraud reporting agency. While international scams can be challenging to prosecute, reporting helps authorities track patterns and warn others. The method of reporting may vary based on your location however the Australian Government tries to simplify this with their website:
https://www.servicesaustralia.gov.au/scams-and-identity-theft?context=60271Share Your Experience - Don’t keep the incident to yourself. Sharing your story with friends, family, and coworkers can help raise awareness and prevent others from falling victim to similar schemes.
Moving Forward
As scams continue to evolve, staying informed is your best defence. By recognizing the warning signs and taking swift action, you can protect yourself and others. For those with an interest and who want to learn more about these scams and how they work there are many easily digestible channels on YouTube that focus on these subjects.
We recommend https://www.youtube.com/@JimBrowning
If you or someone you know has been targeted by a scam, FarSide Tech Repairs is here to help. Contact us for guidance and support in securing your devices and accounts.